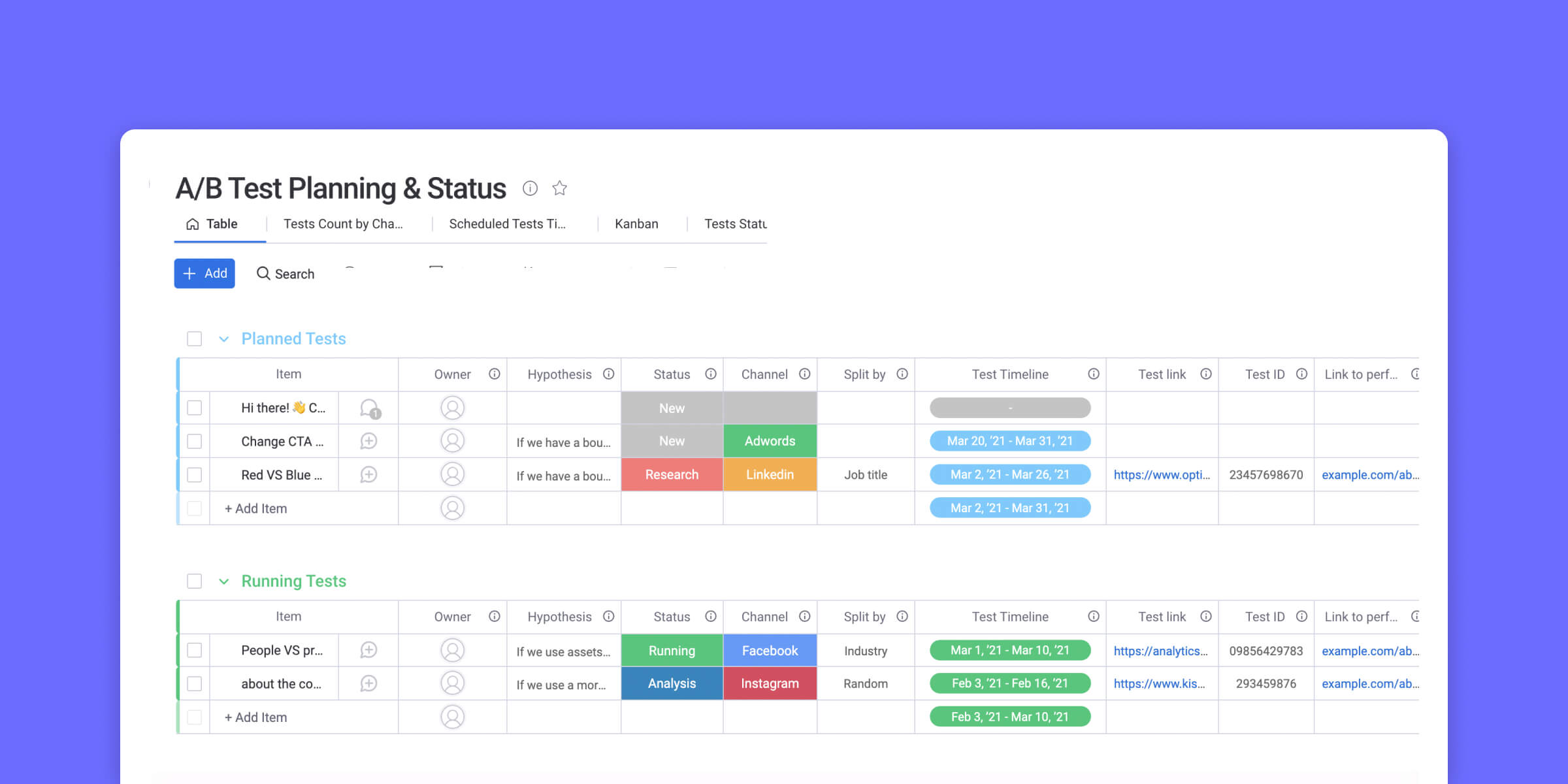
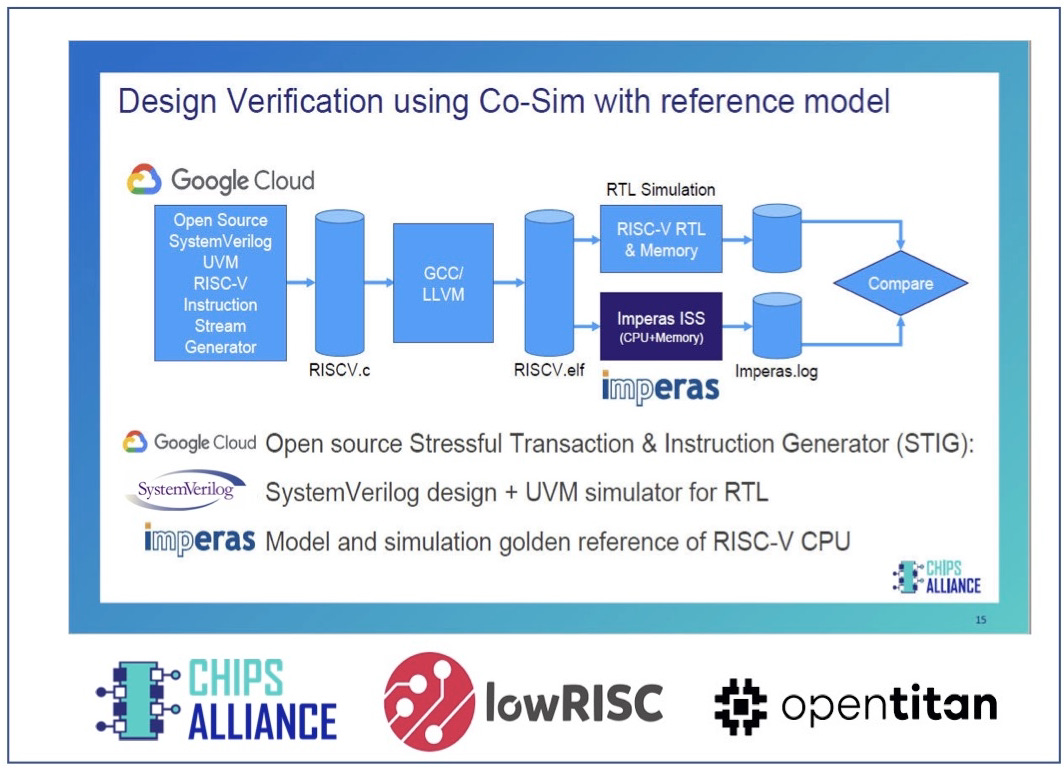
Sensors | Free Full-Text | VerificationTalk: A Verification and Security Mechanism for IoT Applications
Testing the New Version of the Windows Security Events Connector with Azure Sentinel To-Go! - Microsoft Community Hub

Part I - Conducting Customer Research | Guidebook on Conducting Airport User Surveys and Other Customer Research |The National Academies Press